Trojan programs. What is a Trojan virus? The Casbaneiro Trojan hunted for the cryptocurrency of Brazilian and Mexican users
The modern virtual world, with its daily increasing volume of information exchange and electronic payments, has long been favored by criminals. One of the ways cybercriminals make money is by distributing Trojan programs. We will talk about what it is and how hackers earn millions of dollars in profits with the help of Trojans in this article.
So, Trojan horse it is a small program disguised as harmless software. This disguise allows it to enter the computer without hindrance from the user or antivirus program for the malicious actions for which it was created. The name “Trojan program” (Trojan, Trojan, Trojan virus) comes from the legendary “Trojan Horse”, with the help of which Odysseus’s wars got inside Troy.
A Trojan can contain both viruses and worms, but unlike them, it does not spread on its own; there is a person behind it. Of course, it is very rare for a hacker to download a Trojan onto your computer himself. More often than not, it encourages users to download malware onto their computer. How does this happen? The cybercriminal uploads the Trojan program to visited sites, file hosting services and other resources. From there, for various reasons, users download the Trojan onto their computer, infecting it.
Another way to “let Trojan horse” to your computer is reading spam mailings. Typically, a PC user automatically clicks on attached files in emails. Double click and the Trojan program is installed on your computer.
There are several types of Trojan programs:
Trojan-PSW (Password-Stealing-Ware)– a type of Trojan program that steals passwords and sends them to the virus distributor. The code of such a Trojan contains an e-mail address to which the program sends passwords and phone numbers read from the computer. credit cards, telephone numbers and other information. In addition, another target of Trojan-PSW is codes for online games and registration codes for licensed programs.
Trojan-Clicker– a type of Trojan program that performs unauthorized redirection of users to an Internet resource desired by a cybercriminal. This is done to achieve one of three goals: a DDoS attack on a selected server, increasing visitors to a given site, or attracting new victims for infection with viruses, worms or other Trojans.
Trojan-Downloader And Trojan-Dropper– malware with a similar effect. Trojan-Downloader, as the name suggests, downloads infected programs to the PC, and Trojan-Dropper installs them.
Trojan-Proxy– Trojan proxy servers. These programs are used by attackers to secretly send spam.
Trojan-Spy– spyware. The purpose of such Trojan programs is to spy on a PC user. The Trojan takes screenshots of the screen, remembers information entered from the keyboard, etc. These programs are used to obtain data about electronic payments and other financial transactions.
ArcBomb– archives that interfere with the correct operation of the computer. They fill HDD a large amount of duplicate data or empty files, which causes the system to freeze. Hackers use ArcBomb to slow down or stop mail servers.
Rootkit– program code that allows you to hide the presence of a Trojan program in the system. Rootkit without a Trojan is harmless, but together with it it carries a significant danger.
Trojan Notifier– a Trojan program that sends a notification to the creator about a successful attack on the user’s computer.
Cybercriminals unite several computers infected with Trojans into botnets - networks of computers controlled by hackers. Such botnets are a great danger to users. With their help, cybercriminals send spam, steal passwords to bank accounts, and carry out DDoS attacks. Now imagine that one of the computers united in a botnet is yours. Moreover, you will not know anything about this until one “fine” day the police from the cybercrime department knock on your door. Then prove that it was not you who DDoS or the server that was attacked, but a hacker who had access to your system using a Trojan.
In order to minimize (namely, minimize, cannot be avoided) the consequences of infection of your home computer, install a licensed anti-virus program that will update its databases. The creators of anti-virus programs are always several steps behind the hackers, so the databases should be updated as often as possible. If your computer has become infected with a virus, then it needs computer help. We advise you to contact the best service in the city of Kemerovo.
The development of malware requires resources no less, or even several times more, than the development of software needed for operation. Trojans are a simple and, most importantly, cheap method used by hackers to remotely control your software. The fight against Trojans must reach new level, otherwise the creators of antiviruses will not be able to cope with the growing force of cybercrime on their own.
Today on the World Wide Web you can find so many underwater reefs in the form of viruses that you can’t even count them. Naturally, all threats are classified according to the method of penetration into the system, the harm caused and methods of removal. Unfortunately, one of the most dangerous is the Trojan virus (or Trojan). We will try to consider what this threat is. Ultimately, we’ll also figure out how to safely remove this crap from a computer or mobile device.
"Trojan" - what is it?
Trojan viruses are a self-copying type with their own executable codes or embedded in other applications, which pose a fairly serious threat to any computer or mobile system.
For the most part, those most affected are Windows systems and Android. Until recently, it was believed that such viruses did not affect UNIX-like operating systems. However, just a few weeks ago, Apple mobile gadgets were also attacked by the virus. It is believed that the Trojan poses a threat. We will now see what this virus is.
Analogy with history
Comparison with historical events not by chance. And before we figure it out, let’s turn to Homer’s immortal work “The Iliad,” which describes the capture of rebellious Troy. As you know, infiltrate the city in the usual way or it was impossible to take it by storm, so it was decided to give the residents a huge horse as a sign of reconciliation.

As it turned out, there were soldiers inside it, who opened the city gates, after which Troy fell. The Trojan program behaves in exactly the same way. The saddest thing is that such viruses do not spread spontaneously, like some other threats, but purposefully.
How does the threat enter the system?
The most common method used to penetrate a computer or mobile system is to disguise itself as some kind of attractive or even standard program for the user. In some cases, a virus may embed its own codes into existing applications (most often these are system services or user programs).

Finally, malicious code can enter computers and networks in the form of graphic images or even HTML documents - either arriving as email attachments or copied from removable media.
With all this, if the code is embedded in a standard application, it can still partially perform its functions, while the virus itself is activated when the corresponding service is launched. It’s worse when the service is at startup and starts with the system.
Consequences of exposure
Regarding the impact of the virus, it may partially cause system crashes or interruption of Internet access. But this is not his main goal. The main task of the Trojan is to steal confidential data for the purpose of using it by third parties.
Here you will find PIN codes for bank cards, logins with passwords for access to certain Internet resources, and state registration data (numbers and personal identification numbers, etc.), in general, everything that is not subject to disclosure, according to the opinion of the owner of the computer or mobile device (of course, provided that such data is stored there).

Alas, when such information is stolen, it is impossible to predict how it will be used in the future. On the other hand, you don’t have to be surprised if one day they call you from some bank and say that you have a loan debt, or all the money will disappear from your bank card. And these are just flowers.
on Windows
Now let's move on to the most important thing: how To do this is not as easy as some naive users believe. Of course, in some cases it is possible to find and neutralize the body of the virus, but since, as mentioned above, it is capable of creating its own copies, and not just one or two, finding and removing them can become a real headache. At the same time, neither a firewall nor standard anti-virus protection will help if the virus has already been missed and infiltrated into the system.
In this case, it is recommended to remove the Trojan using portable anti-virus utilities, and in the case of RAM capture, with special programs loaded before starting the operating system from an optical media (disk) or USB device.

Among portable applications, it is worth noting products like Dr. Web Cure It and Kaspersky Virus Removal Tool. Of the disk programs, Kaspersky Rescue Disc is the most functional. It goes without saying that their use is not a dogma. Today you can find any amount of such software.
How to remove a Trojan from Android
As for Android systems, things are not so simple. Portable applications have not been created for them. In principle, as an option, you can try connecting the device to a computer and scanning the internal and external memory with a computer utility. But if you look at reverse side medals, where is the guarantee that when connected, the virus will not penetrate the computer?
In such a situation, the problem of how to remove a Trojan from Android can be solved by installing the appropriate software, for example from Google Market. Of course, there are so many things here that you are simply at a loss as to what exactly to choose.

But most experts and specialists in the field of data protection are inclined to think that the best application is the 360 Security application, which is capable of not only identifying threats of almost all known types, but also providing comprehensive protection mobile device in the future. It goes without saying that it will constantly hang in RAM, creating an additional load, but, you see, security is still more important.
What else is worth paying attention to
So we have dealt with the topic “Trojan - what is this type of virus?” Separately, I would like to draw the attention of users of all systems, without exception, to a few more points. First of all, before opening email attachments, always scan them with an antivirus. When installing programs, carefully read the proposals for installing additional components such as add-ons or browser panels (the virus can be disguised there too). Do not visit dubious sites if you see an antivirus warning. Do not use the simplest free antiviruses (it is better to install the same Eset Smart Security package and activate using free keys every 30 days). Finally, store passwords, PIN codes, bank card numbers and everything else in encrypted form exclusively on removable media. Only in this case can you be at least partially confident that they will not be stolen or, even worse, used for malicious purposes.
A Trojan (Trojan virus or Trojan horse) is a type of malicious software that masquerades as legitimate software. It is often used by cybercriminals to steal personal data, track users, and gain unauthorized access to systems.
If you've paid any attention to computer and Internet security in the last ten years, you've undoubtedly come across the term "Trojan horse." You probably know that you should not expect anything good from these malicious programs, but you may not know what they can do to your computer, how they get into it and how to prevent it. By understanding what a Trojan is and what problems it can cause you, you can avoid encountering these dangerous malware samples.
What is a Trojan virus?
The term is somewhat imprecise, but it is commonly used in place of the more correct term "Trojan". The virus infects ordinary computer files - it hijacks a single file and destroys or maliciously modifies it in the process. It will then try to spread to other computers, infecting other files.
Unlike viruses, Trojans are programs; they do not need to manipulate another file to do their dirty work. In addition, they are incapable of self-reproduction. But don’t be fooled: the consequences of Trojans’ actions can be as destructive as any computer virus.
Just like the story of the Trojan horse from ancient Greek mythology, the Trojan malware appears in the “image” of what you want. It often disguises itself as free software or an email attachment, and then once you give it permission to install on your computer, it opens the floodgates.
Once a Trojan has access to your computer, it can do whatever it wants, but most of these malware aim to gain complete control over your computer. In other words, all your actions on the computer are recorded and sent to the server specified by the Trojan. This is especially dangerous if you perform financial transactions on your computer, since the Trojan program sends information about your bank card or payment details to people who may use or sell it. With the help of Trojans, attackers can turn your computer into a zombie and use it to launch cyber attacks around the world.
How to protect yourself from Trojans
Trojans are so named because they require your permission to run on your computer - either when you run a program yourself, or when you open a document or image, which then launches a program. Based on this, the first and best defense against Trojans is to never open an email attachment or run a program unless you are 100% sure of the source of the files downloaded from peer-to-peer programs or websites. But in today's interconnected world, this is rarely possible, so there are a few specific security measures that need to be taken.
Always update your software. This goes double for important programs like your operating system and browser. in these types of programs, and through them Trojans are sent to your computer, which do their dirty work. The software manufacturer will usually release patches for these vulnerabilities, but they won't do you any good unless you keep the software on your device up to date. To keep your Internet connection as secure as possible, your firewall should always be turned on. Both software and hardware firewalls do an excellent job of filtering out malicious traffic and can often prevent Trojans from being downloaded onto your computer.
All this is useful, but to completely protect yourself, you should install antivirus software or a Trojan removal utility. This software (provided it is updated regularly) scans your system for Trojans and automatically checks any program or file you run to ensure its safety. There are free Trojan removal utilities available on the Internet, but few are regularly updated, and some are even Trojans themselves. To better protect your computer, use reputable antivirus software with a free trial. This will allow you to evaluate the benefits of a particular program before purchasing it. Such programs are often included in a general security package, but at the same time they give you the opportunity to specify the protection functions you need and disable those you don’t need.
Protecting your computer from Trojans doesn't have to be an overwhelming task. Following several simple rules safe online behavior and using a reliable security solution, you can be sure that your computer is protected from the vast majority of Trojans and other malware.
The expression “Trojan horse” comes from history, and we still use it in conversation today. The expression "Trojan horse" refers to something that at first glance looks quite common and innocent, but, in fact, can cause harm. A Trojan virus (or also called a Trojan) is a file that looks quite harmless, but, in fact, poses a threat. Although they appeared relatively recently, they have already become entrenched in our lives and their reputation has eclipsed the wooden Trojan horse from the distant past. Next, we will describe some of the types of Trojan viruses that you may encounter.
The first Trojan virus we will discuss comes under the “trap” category. It is also better known as Spy Sheriff, and has already managed to infect millions of computer systems around the world. This Trojan virus is classified as malware. It does not affect or harm the computer system, but it does cause all sorts of annoying pop-ups to appear.
Most of these windows appear as system messages that contain warnings stating that you must install some type of software. Once Spy Sheriff gets onto your computer, it is very difficult to remove. If you try to remove it in the usual way, it will simply re-install itself using the hidden files that it has infected on your system. Most antivirus and antispyware programs will not be able to detect this virus. It also cannot be removed using System Restore because it controls the components that control this feature in Windows.
Sometimes Trojan viruses can be contained in archives that appear harmless. Some Trojans are used by attackers to remotely control someone else's computer. They are also used to attack and hack computer systems. One of the most famous cases involving Trojan involved a professor on whose computer thousands of child pornographic photographs were found. At first he was accused of knowingly downloading them. Although, ultimately, he was acquitted and it turned out that this was the action of Trojan, the situation still turned out to be very unpleasant.
Another famous type of virus problem that has made its mark on history is the Vundo virus. This virus uses Windows memory at various intervals and creates pop-up windows indicating that important system files have been lost. It also triggers a lot of messages telling you that you should install several security software, many of which are actually viruses. Fortunately, this virus is easy to remove, as there are many automatic programs on the market for this process.
Trojan virus may different ways get into your computer system. But one thing you must remember: they cannot be activated unless you activate the file in which they are hidden. This is why it is so important to check unknown files and, if possible, not open them at all, because if a Trojan appears in the system, this can lead to dire consequences
A Trojan is a type of worm virus that can cause serious damage to your computer. A worm is a program that at first glance may seem harmless and safe, but in fact, it contains something very harmful to your computer. So harmful that it can destroy your computer through widespread damage that may be irreversible.
If you remember history well, then it will not be difficult for you to remember how the Greeks won Trojan War, hiding in a large hollow wooden horse in order to enter the well-fortified Troy. In reality, the Trojan also gains access to your computer. Trojans enter your computer when you download safe programs such as games, images, music or video files, but as soon as these programs are executed, the Trojans begin their work. Trojans can do not only things that will greatly annoy you; but they can also seriously damage your computer. Trojans can also wipe your disk, send your credit card numbers and passwords to strangers, or allow others to use your computer for illegal purposes, such as denying service protection, thereby damaging networks.
Your best defense is antivirus software that is automatically updated and closely monitors what you download from the Internet. With antivirus software, you only download what is safe from websites, thereby protecting your computer from viruses. Antivirus software is your best defense not only against Trojan viruses, but against much more - protecting you from spyware, adware, and other types of malicious attacks on your computer. With good antivirus software, you won't have to worry about losing your data or missing personal information.
Disguised malware
No matter what protective measures are taken, no network can be protected from one serious danger - human gullibility. This is exploited by malware called Trojan horses, whose malicious codes are hidden inside something completely harmless. But if the program was installed voluntarily, it can overcome any firewalls, authentication systems and virus scanners.
Trojan horses differ from each other in the harmful actions they perform once inside a computer. This can be either a harmless prank associated with displaying some obscenity or political slogan on the screen, or a real information disaster, leading to the destruction of data on the disk and damage to equipment. Some of the Trojan horses, combined with viruses, spread between systems via e-mail.
The most sophisticated ones act very treacherously and do not limit themselves to causing damage to the system. In addition to hacking, Trojan horses can be used to spy on people and act like real criminals, albeit virtual ones. No one can feel safe. In the fall of 2000, Microsoft suffered a highly publicized hacker attack in which the source code for a future product was stolen and possibly modified. operating system. This was the result of the introduction of a “Trojan horse” that concealed a “worm” - a program that “crawled” across the network and copied itself to other computers. Once installed on one of Microsoft's computers, the program began to spread across the network and did so until it reached a computer that contained important secret information. After this, the “Trojan horse” signaled its presence to the hacker and opened a “secret door” on the network.
So what can you do to avoid Microsoft's fate? Of course, you cannot expel all users from the network. However, there are several ways to minimize the risk, starting with vigilance and education. Regular backup is a necessary procedure for restoring information after exposure to those “Trojan horses” whose intervention is limited to data destruction. Using a full suite of security software, such as firewalls and virus scanners, can help catch some of the more notorious offenders. But the most important thing is to learn for yourself and explain to network users what “Trojan horses” are, how they operate and what type of programs they can hide. In addition, you need to figure out how to distinguish a Trojan horse from a real gift horse before it gets into your network.
Dark horses
Apart from Bubbleboy, which was very rare and penetrated through a now-fixed security hole in Microsoft Outlook, the virus is almost impossible to catch just by reading an email message. The user must be tricked into running the attached file, and virus creators have good reason to believe that this is not so difficult to do. Many people automatically double-click any file they receive via email, so they need to get into the habit of doing otherwise.
As you know, Windows files with the extensions *.com (command), *.exe (executable) and *.dll (dynamic link library) are programs. They have the potential to do almost anything to the system, so they need to be handled with extreme caution, i.e. they should only be run if the source you got them from is completely trustworthy and you know for sure What are these programs intended for? The fact that a program was emailed to you by a friend or colleague is not enough reason to run it. A Trojan horse could have infiltrated your friend's email system and sent itself to every address in your address book.
To prevent virus infections, many organizations have policies in place to prevent users from installing unauthorized software. However, these types of restrictions are often difficult to enforce and can prevent employees from using the truly best software on the market to do their jobs. Whether you enforce such rules or not, it is important that users are aware of the potential dangers. If employees are allowed to download programs, they must know which ones pose the greatest threat. If this is forbidden to them, then they will pay more attention to the rules, understanding what dictates them.
Pirated software poses the most serious threat because the source from which it comes is, by definition, untrustworthy. Serious programmers have long been sharpening their grudge against pirates who distribute Trojan horses under the guise of illegal programs. The first known attack on the Palm platform fell into this category, carried out using a program presented as an emulator of the popular GameBoy program called Liberty. Instead of the promised emulation, it deletes all files and applications.
The most dangerous type of files are system fragment files, the purpose of which is to transfer parts of documents between applications and the desktop (shell scrap object) - they seem to be specially created for use as a “Trojan horse”. Although they should have a *.shs or *.shb extension, they remain hidden in the Windows 98/Me environment, masquerading as any other file type. The first program to exploit such a vulnerability was the Stages virus, which appeared in June 1998. Pretending to be a harmless text file, it was actually a Visual Basic script and sent itself by email to everyone listed in the user's address book.
Fragment files are so dangerous that the Symantec Antivirus Research Center recommends against using them altogether. Since very few legitimate applications deal with these files, many users could easily do without them altogether by deleting the schscrap.dll file from the Windows/system directory on their PC. As a less drastic measure, you can prevent the system from hiding such files by deleting the HKEY_CLASSES_ROOT\ShellScrap registry entry.
Pulling on the reins
No matter how serious a threat viruses and worms pose, they are still not the most dangerous content that can be hidden in Trojan horses. Many of them are designed to gain access to your network and hide small server programs that operate almost unnoticed. With the help of these programs, a hacker can find out your secrets or even take control of your PC.
The most unscrupulous hacking tool is Back Orifice 2000, often simply called BO2K, created by the hacker team “Dead Cow Cult”. The authors define their program as a “remote administration tool” that allows you to control a computer without the user’s knowledge or consent. It can run almost unnoticed under any version of Windows, providing an unauthorized user with almost complete access to the system. In addition to copying and changing the contents of files, hackers armed with BO2K can record every user action and even receive a stream of video information from his screen in real time.
Ironically, the Cult of the Dead Cow team themselves became victims of the Trojan Horse. The first CDs of Back Orifice 2000 intended for distribution were infected with the terrible Chernobyl virus, which could cause irreversible damage to the equipment. Aspiring hackers attending the 1999 DefCon conference found that instead of gaining control of other people's computers, they lost control of their own as their hard drives were overwritten and their BIOS chips were wiped.
The attack on Microsoft in the fall of 2000 used a Trojan horse called QAZ, which masqueraded as the Notepad utility and was located in the file notedad.exe. The original Notepad program was still available, but was renamed note.exe so that users did not notice the changes. An administrator, knowing that this file was not included in the standard Windows installation, could delete it, causing Notepad to stop working while the Trojan horse remained intact.
Even if attackers are not interested in your information, gaining control of your computers is still a serious threat. The Distributed Denial of Service (DDoS) attacks that took down some popular Web sites in early 2000 were carried out using Trojan horses. These programs rely on thousands of computers working together, so they can't just run on just one of them. However, an attack becomes possible when one computer gains control over thousands of others.
The consequences of your participation in attacks like DDoS go beyond the fact that you are disapproved of as a member of the online community and your organization is at risk of litigation. For example, as a result of attacks on Yahoo! and eBay suffered not only from these servers, but also from thousands of home and office users whose computers were involved in these attacks. If your mail server is busy attacking, it will not be able to fulfill its main purpose.
Any PC connected to a telephone line is a potential target for financially motivated attacks, since its modem can be reprogrammed to call high-value phone numbers. There are known “Trojan horses” that replace a regular telephone number in the user’s dial-up access settings with an international one, calls to which can cost several dollars per minute. And if this number is actually connected to an Internet provider, the victim may not notice anything until he receives his phone bills.
This type of Trojan horse first appeared in 1998, when thousands of users in Europe downloading pornographic slideshows discovered that their modems were calling a very expensive number in the Republic of Ghana. The attack was ranked No. 3 on the Federal Trade Commission's list of the worst Internet scams and is considered more dangerous than phone piracy and pyramid schemes.
Close the door tightly
Most Trojan horses signal their presence to a hacker through a given TCP port, so a properly configured firewall can detect and block them. Lists of ports used by popular Trojan horses are published on special Web sites (see the Internet Resources sidebar), some of which can even perform scanning. However latest versions Many malicious programs can change the specified port, making them difficult to detect. Antivirus software can also detect Trojan horses, although this comes with its own risks. Because such software must be updated regularly, the antivirus software company gains access to your network. In November 2000, an update to Network Associates' McAfee VirusScan software caused some systems to crash and cause the loss of unsaved data. This was due to a bug in the software rather than a deliberate act, but for already compromised companies such as Microsoft entering the antivirus software market, there is a risk that individual Trojan horses could exploit this method attacks.
The German government believes that Windows 2000 may already be harboring a Trojan horse. It has gone so far as to threaten to ban the distribution of this software until Microsoft removes the Disk Defragmenter utility, which allegedly hides this dangerous code. Microsoft declined to do so, but published detailed instructions on its German support site explaining to users how to uninstall the utility themselves. Those managers who are concerned about this fact should keep in mind that there is still no evidence that the mentioned “Trojan horse” even exists. In fact, the US government is so confident in the security of Windows 2000 that it uses the software in many of its organizations, including the military.
Although the press and some users often refer to any piece of malware as a virus, security experts know that this is not the case. Here short description the three most common types of malware, each of which can be hidden inside a Trojan horse.
A virus is a self-replicating code that attaches itself to another file in the same way that real viruses attach to living cells. Initially, viruses attacked program files with *.com or *.exe extensions, but the spread of scripting languages allowed them to infect office documents and even email messages.
A worm is a stand-alone program that typically reproduces itself by copying itself to other computers on the network. They are sometimes called bacteria because they are independent of other programs. The most widespread program is happy99.exe, which paralyzed many computers two years ago and still appears occasionally - especially around New Year.
The logic bomb does not play, but can cause serious damage. These are usually simple programs that perform harmful functions, such as deleting user files when executed. The modern Internet is not only an extremely useful information environment, but also a potential source of various dangers that threaten both the computers of ordinary users and servers. And if you believe the statistics, the most serious of these threats are viruses, especially the so-called Trojan horses. The origin of this term is known to everyone from school history courses. He identifies a gift that poses some kind of threat to its recipient. In principle, this very accurately describes this class of malware. These "gifts" can cause serious harm to Internet users. Well, in order not to be unfounded, let us, dear readers, consider the action Trojan horses in more detail.
Trojan horses- this is one of the most dangerous threats to a computer and its owner on the Internet
Remote administration
Remote administration Trojans allow a hacker to control the victim computer
Today you can find many programs that allow you to remotely administer both individual computers and entire computer systems. These are very convenient utilities that significantly simplify the task of local network administrators and save their time (and therefore companies’ money). The operating principle of such programs is simple. A special agent is installed on the remote PC. After this, the administrator can launch the main module on his machine at any time, connect to another computer and be able to fully manage it.
Now imagine that a personal computer user does not know about the agent installed on his system. And the latter communicates not with a machine neighboring on the local network, but with a PC remote thousands of kilometers away, behind which a hacker is sitting. In this case, the attacker can do anything: obtain passwords, copy personal documents, install any software, simply reboot or turn off the computer... That's why Trojan horses(actually these are agents of remote administration utilities) of the considered class are considered the most dangerous. They provide the attacker with virtually unlimited possibilities to control the victim’s machine.
Data theft
Some Trojans can steal user passwords
To another extremely dangerous group Trojan horses include those that are aimed at stealing information from users. They pose a particularly serious threat to home PC owners. It would seem that everything should be quite the opposite. Well, what can Do ordinary users have secret data? Much more interesting to hackers should be companies, each of which is full of trade secrets, and they can always try to sell them to competitors. However, there is one problem. After all Trojan the horse cannot independently find files with secret documentation. In addition, it is quite difficult to transmit any significant amounts of data over the Internet without being noticed. But from the computers of home users (often less secure), it is easy to steal, for example, passwords for accessing the operating system or the Internet.
Moreover, it was the last option that gained the most popularity. By using Trojan horses that steal passwords to access the Network, attackers who are connected to the same provider as the victim, can It's easy to pass on your Internet costs to other people simply by using their login credentials. In addition, sometimes there are malicious programs with a rather complex algorithm that can try to retrieve passwords saved in the browser from various web services, FTP servers, etc.
Espionage
Spy Trojans allow a hacker to obtain detailed information about the user, including his passwords for various services.
Today, attackers are increasingly using espionage. Its essence is as follows. A special agent is installed on the victim’s computer, which, working unnoticed by the user, collects certain information about him and sends it to the hacker via the Internet. They even came up with a special term for such software - spyware. Modern spyware can do a lot: keep a log of the keys pressed by a person on the keyboard, periodically take screenshots of the entire screen and the active window, record the names of running programs, open documents and addresses of visited web pages.
All this allows attackers to obtain very detailed data about their victim, including the passwords needed to access the Internet and use various services.
However, in fairness it is worth noting that the vast majority Trojan spying horses record only the sequence of keys pressed. Firstly, this is the most critical information. This is how you can find out user passwords, for example, for various online services: email, online stores, etc. And having received them, the attacker will be able to safely use these resources in the future on behalf of the victim. Secondly, the list of pressed keys takes up a relatively small volume. And the less data, the easier it is to quietly transfer it to a hacker’s computer.
Page transitions
Some Trojans force the user to open certain websites
There are quite a few affiliate programs on the Internet today. Their essence is as follows. A person attracts visitors to the sponsor’s website, for each of whom he receives a small reward. In principle, affiliate programs are an absolutely normal phenomenon. But only as long as both parties follow the rules and adhere to generally accepted norms. Meanwhile, many resources with “adults only” content turn a blind eye to the actions of their partners, as a result of which the following happens.
Some people use Trojan horses. That is, they infect the computers of Internet users with such malicious programs that constantly change the home page in the browser to the address of the partner’s website, when going to which several more pop-up windows with sponsors’ web projects immediately open. In addition, such Trojan horses capable of independently initiating the opening of the address specified by them upon the occurrence of certain events (connecting to the Internet, opening a new browser window, etc.).
Carrying out attacks
Trojan horses used to carry out DDoS attacks
Therefore, most often, attackers act according to the following scheme. First they infect with a special Trojan horse as many machines as possible of ordinary Internet users. This malicious program lives on the PC for the time being, without revealing itself in any way and without performing any destructive actions. However, upon receiving a special command from the control center, the Trojan is activated and begins sending the packets required for the attack to the specified victim. And since there can be hundreds and thousands of such computers, it is not surprising that the server “crashes”. Basically for the user himself Trojan horses This class is practically not dangerous. Except for the moment that during their work his channel is loaded quite seriously. In addition, few Internet users will enjoy the fact that he actually became an accomplice in the crime.
Trojan horses can used to download other malicious software onto the user’s computer and install it
Recently, the requirements for malware have changed. If earlier all viruses were very small, then modern ones Trojan horses can be large enough. This is due to their great functionality (for example, spyware and remote administration utilities) and the technologies used. Meanwhile, it is not always possible to unnoticedly download such volumes of information onto the user’s computer. Therefore, hackers began to use the following technique. First, the PC is infected with a rather small utility that establishes a connection with a specific server, downloads other malicious software from there, installs and runs it. Universal loaders are especially dangerous in this regard. They allow an attacker to install different Trojan horses or even a whole bunch of them. It all depends on what is currently on the specified server.
Let's sum it up
So, as you and I, dear readers, have seen, modern Trojan horses really pose a serious threat to the security of any computer connected to the World Wide Web. Moreover, it is necessary to take into account that today there are programs related to two, three, or even more classes at once. Such Trojans can, for example, spy on a user, secretly download and install other software on his computer, and participate in attacks. Meanwhile, protecting yourself from this threat is generally not difficult. A regularly updated anti-virus program, a properly configured firewall and periodic updates of the operating system and software used are quite enough for this.
Trojan program. (also - Trojan, Trojan, Trojan horse) is a malicious program used by an attacker to collect information, destroy or modify it, disrupt the operation of a computer or use its resources for unseemly purposes. The effect of a Trojan may not actually be malicious, but Trojans have earned their notoriety for their use in the installation of programs such as Backdoor. Based on the principle of distribution and action, a Trojan is not a virus, since it is not capable of self-propagation.
The Trojan program is launched manually by the user or automatically - by a program or part of the operating system running on the victim computer (as a module or utility program). To do this, the program file (its name, program icon) is called a service name, disguised as another program (for example, installing another program), a file of a different type, or simply given an attractive name, icon, etc. for launching. A simple example The Trojan may be the program waterfalls.scr, whose author claims that it is a free screen saver. When launched, it loads hidden programs, commands and scripts with or without the user's consent or knowledge. Trojan horses are often used to trick security systems, leaving the system vulnerable, thereby allowing unauthorized access to the user's computer.
A Trojan program can, to one degree or another, imitate (or even completely replace) the task or data file it is disguised as (installation program, application program, game, application document, picture). In particular, an attacker can assemble an existing program with Trojan components added to its source code, and then pass it off as the original or replace it.
Similar malicious and camouflage functions are also used by computer viruses, but unlike them, Trojan programs cannot spread on their own. At the same time, a Trojan program can be a virus module.
Etymology
The name "Trojan" comes from the name "Trojan horse" - wooden horse, according to legend, given by the ancient Greeks to the inhabitants of Troy, inside which the soldiers were hiding, who later opened the gates of the city to the conquerors. This name, first of all, reflects the secrecy and potential insidiousness of the true intentions of the program developer.
Spreading
Trojan programs are placed by the attacker on open resources (file servers, writable drives of the computer itself), storage media, or sent via messaging services (for example, e-mail) with the expectation that they will be launched on a specific, member of a certain circle, or arbitrary " target computer.
Sometimes the use of Trojans is only part of a planned multi-stage attack on certain computers, networks or resources (including third parties).
Trojan body types
Trojan program bodies are almost always designed for a variety of malicious purposes, but can also be harmless. They are broken down into categories based on how Trojans infiltrate and cause harm to a system. There are 6 main types:
1. remote access;
2. destruction of data;
3. bootloader;
4. server;
5. security program deactivator;
6. DoS attacks.
Goals
The purpose of the Trojan program can be:
* uploading and downloading files;
* copying false links leading to fake websites, chat rooms or other registration sites;
* interfering with the user's work (as a joke or to achieve other goals);
* theft of data of value or secret, including information for authentication, for unauthorized access to resources (including third systems), fishing for details regarding bank accounts that can be used for criminal purposes, cryptographic information (for encryption and digital signature);
* file encryption during a code virus attack;
* distribution of other malicious programs such as viruses. This type of Trojan is called Dropper;
* vandalism: destruction of data (erasing or overwriting data on a disk, hard-to-see damage to files) and equipment, disabling or failure to service computer systems, networks, etc., including as part of a botnet (an organized group of zombie computers), for example , to organize a DoS attack on the target computer (or server) simultaneously from many infected computers or send spam. For this purpose, hybrids of a Trojan horse and a network worm are sometimes used - programs that have the ability to quickly spread across computer networks and capture infected computers in a zombie network.;
* collecting email addresses and using them to send spam;
* direct computer control (allowing remote access to the victim computer);
* spying on the user and secretly communicating information to third parties, such as, for example, website visiting habits;
* registration of keystrokes (Keylogger) for the purpose of stealing information such as passwords and credit card numbers;
* obtaining unauthorized (and/or free) access to the resources of the computer itself or third resources accessible through it;
* Backdoor installation;
* using a telephone modem to make expensive calls, which entails significant amounts of telephone bills;
* deactivating or interfering with the operation of anti-virus programs and firewalls.
Symptoms of Trojan infection
* appearance of new applications in the startup registry;
* displaying fake downloads of video programs, games, porn videos and porn sites that you did not download or visit;
* taking screenshots;
* opening and closing the CD-ROM console;
* playing sounds and/or images, demonstrating photographs;
* restarting the computer while an infected program is starting;
* random and/or random shutdown of the computer.
Removal methods
Because Trojans come in many types and forms, there is no single method for removing them. The simplest solution is to clean out the Temporary Internet Files folder or find the malicious file and delete it manually (Safe Mode is recommended). In principle, antivirus programs are capable of detecting and removing Trojans automatically. If the antivirus is not able to find the Trojan, boot the OS from alternative source may enable an antivirus program to detect the Trojan and remove it. It is extremely important to regularly update the anti-virus database to ensure greater detection accuracy.
Disguise
Many Trojans can be on a user's computer without his knowledge. Sometimes Trojans are registered in the Registry, which leads to their automatic launch when Windows starts. Trojans can also be combined with legitimate files. When a user opens such a file or launches an application, the Trojan is also launched.
How the Trojan works
Trojans usually consist of two parts: Client and Server. The server runs on the victim machine and monitors connections from the Client used by the attacking party. When the Server is running, it monitors a port or multiple ports for a connection from the Client. In order for an attacker to connect to the Server, it must know the IP address of the machine on which the Server is running. Some Trojans send the IP address of the victim machine to the attacking party via email or other means. As soon as a connection has been made with the Server, the Client can send commands to it, which the Server will execute on the victim machine. Currently, thanks to NAT technology, it is impossible to access most computers through their external IP address. And now many Trojans connect to the attacker's computer, which is set to accept connections, instead of the attacker itself trying to connect to the victim. Many modern Trojans can also easily bypass firewalls on the victim’s computer.
This article is licensed under
 Turkish chocolate cake Note to the hostess
Turkish chocolate cake Note to the hostess Recipes for delicious salads with fried potato strips
Recipes for delicious salads with fried potato strips Baked pike with potatoes Pike in the oven with potatoes and tomatoes
Baked pike with potatoes Pike in the oven with potatoes and tomatoes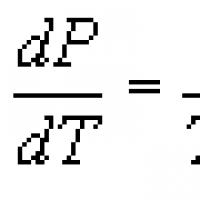 Clapeyron–Clausius equation
Clapeyron–Clausius equation Overpaid wages: actions of the employee and the employer
Overpaid wages: actions of the employee and the employer Green poop in a child: normal or serious danger Green poop for a 6 month old child
Green poop in a child: normal or serious danger Green poop for a 6 month old child Simple and healthy desserts for children
Simple and healthy desserts for children